1.Introduction
Recent large-scale data breaches across major sectors - including telecommunications, retail and finance sectors have sparked significant public concern. Consequently, the National Assembly and government agencies are advancing legislative amendments and stricter regulations to bolster the prevention of—and response to—cybersecurity threatstargeting critical networks and personal data.
In this Legal Update, we examine the legislative bills under deliberation in the National Assembly and highlight the government's latest policy directions.
2.Key Contents of the Proposed Amendments
Cybersecurity incidents relating to information and communications networks are governed by the Act on Promotion of Information and Communications Network Utilization and Information Protection, etc. (the “Network Act”), which falls under the jurisdiction of the Ministry of Science and ICT (the “MSIT”). Meanwhile, personal data breaches are governed by the PersonalInformation Protection Act (the “PIPA”), which is overseen by the Personal Information Protection Commission (the “PIPC”). Although the Network Act and the PIPA are separate legal regimes with different scopes and competent authorities, in practice, hacking incidents often involve the leakage of personal data, and therefore regulatory issues under both statutes commonly arisesimultaneously.
The key provisions of the proposed amendments to the Network Act and the PIPA currently under deliberation by the National Assembly are as follows. Once the bills listed below are passed by the National Assembly plenary session, they will be transferred to the government and promulgated, and will take effect six months after the date of promulgation. However, the provisions concerning information security level assessments will take effect one year after promulgation, and the mandatory implementation of ISMS-P will take effect from July 1, 2027.
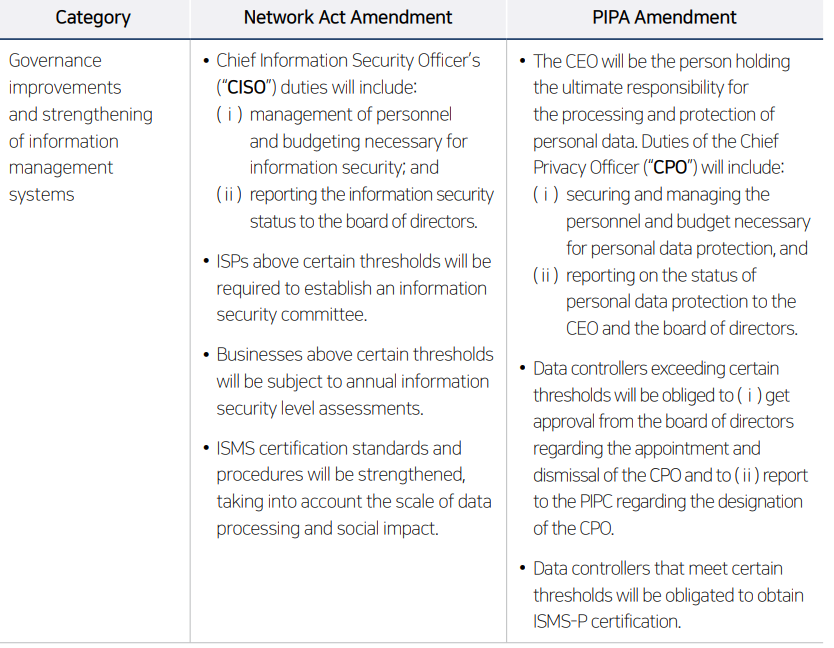
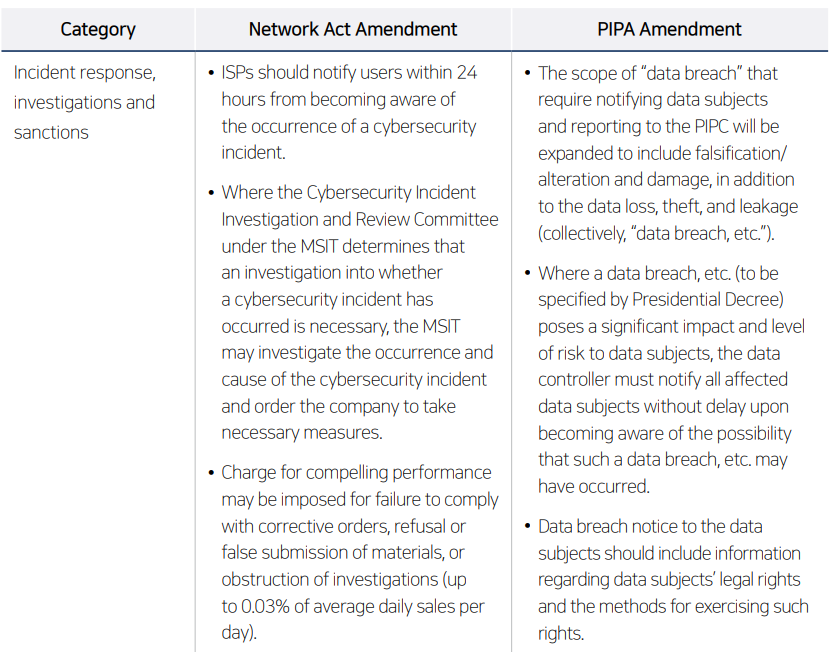
The proposed amendments primarily address (1) the improvement of data protection and security governance and the strengthening of information management systems, and (2) raising the effectiveness of incident response, related investigations and sanctions in the event of security incidents.
The Network Act applies to information and communications service providers (“ISPs”), which means businesses that provide information or mediate provision of information through telecommunications network. This is a broad term that encompasses all types of online and mobile services (e.g. e-commerce, social media, fintech, mobile banking). In this Legal Update, we refer to them as ISPs or companies.
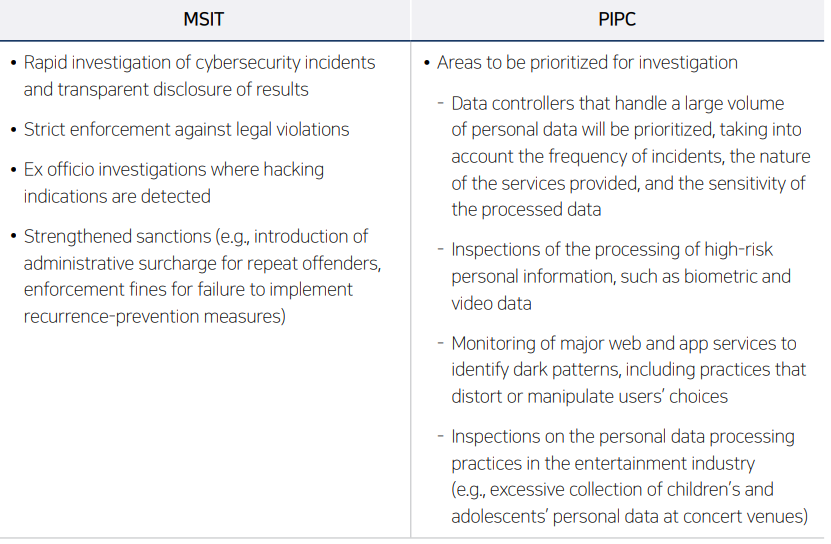
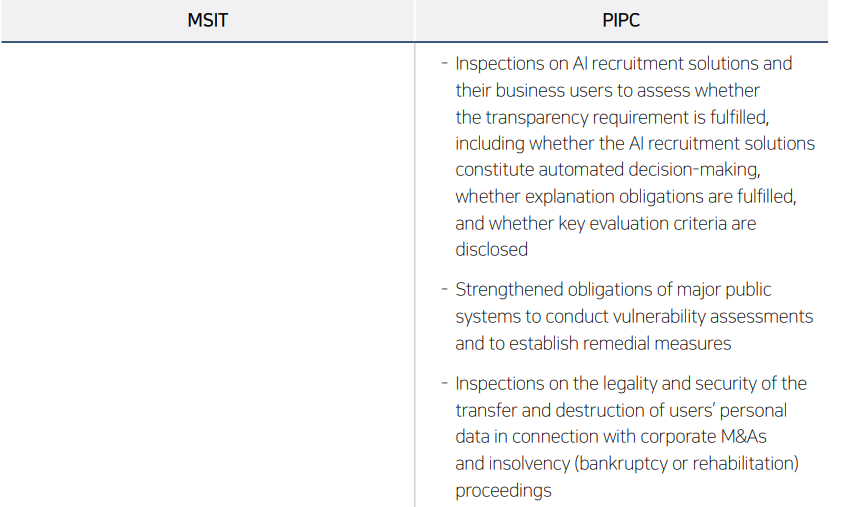
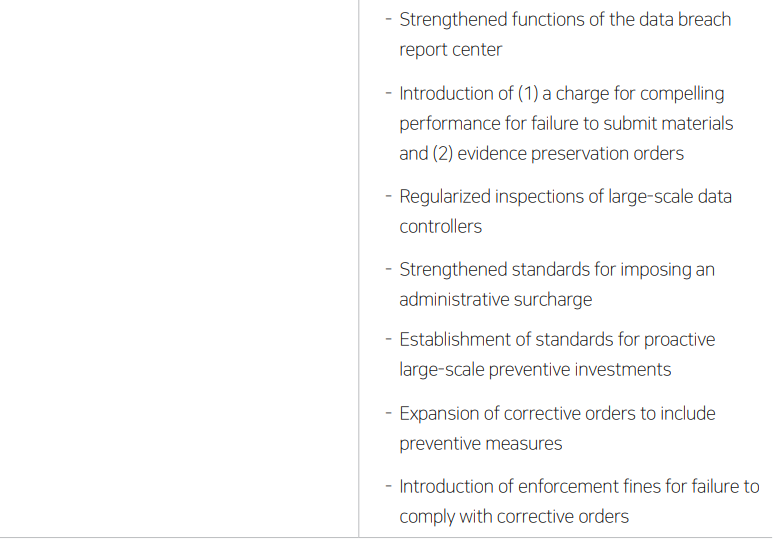
Meanwhile, the MSIT has included “response to hacking incidents in the private sector” as a key issue in its Work Plan for 2026. In addition, the PIPC has disclosed its investigation policy directions, including areas to be prioritized for investigation in 2026 and improvements to investigation systems and procedures. The main points announced by the two authorities are summarized below.
3.Key Takeaways for Businesses
As discussed above, the National Assembly and the government are encouraging companies to take proactive measures to prevent information security incidents while also calling for stronger data protection and information security governance. In light of these regulatory developments, companies should focus their responses on the following areas:
• Assess your current information security status. The proposed amendments contemplatedifferentiated regulatory obligations based on factors such as a company’s revenue size, the nature of its services, the types and volume of personal data processed, and its potential social impact. Therefore, the first step would be to identify the level of regulation applicable to your business and assess your current information security status based on the updated requirements.
• Improve your information security and data protection governance framework. The proposed amendments expand the scope of duties and authority of the CISO and CPO and expressly specify the responsibilities of the company’s representative, thereby strengthening governance requirements. Accordingly, companies should review whether their current information security and data protection governance framework satisfies the enhanced statutory standards and whether the responsibilities and authorities of the CISO and CPO are clearly defined in accordance with the law.
• Invest and strengthen your information security and data protection organization. The proposed amendments strengthen ex ante regulatory oversight, such as regular information security level assessments, mandatory ISMS-P certification, and the obligation to prepare cybersecurity incident management and response manuals. At the same time, they grant CISOs and CPOs the authorityand responsibility to manage personnel and allocate budgets for the necessary information security. Companies should therefore establish a system for operating an information security organization of an appropriate size on an ongoing basis.
In addition to preventive measures, there is a growing need to establish frameworks that enable promptand effective response to cybersecurity and personal data breach incidents.
• Review your incident response policies and align them with statutory requirements. The proposed amendments impose an obligation to prepare cybersecurity incident management and response manuals and expand notification obligations to users and data subjects, thereby strengthening incident response regulations. Companies should proactively assess whether their existing incident response procedures, internal reporting systems, and notification processes satisfy the strengthened requirements and implement necessary improvements.
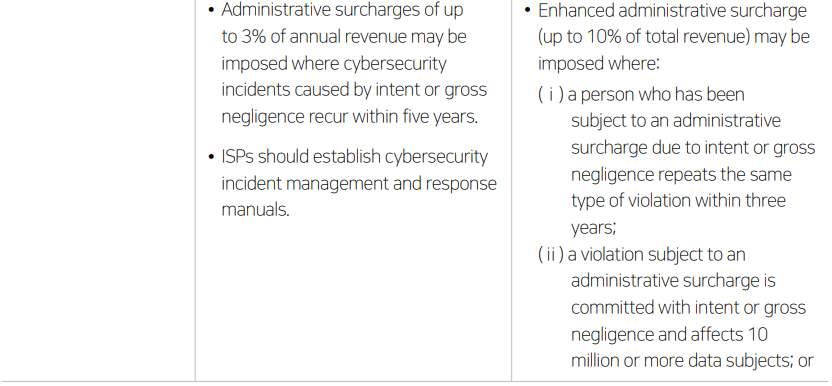
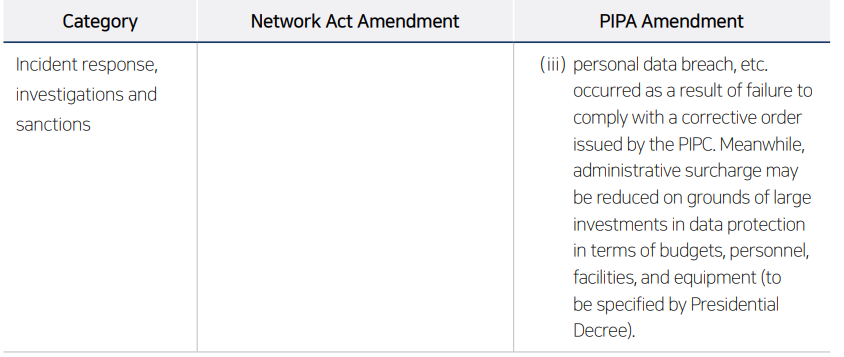
Establish a prompt and effective response system for regulatory authorities’ requests for information, investigations and corrective orders. The proposed amendments strengthen sanctions for failure to comply with corrective orders or refusal to submit materials, and regulatory authorities have indicated that they will strictly enforce sanction provisions to ensure the effectiveness of investigations. Accordingly, companies should refine internal decision-making procedures and response processes to enable prompt and appropriate responses to regulatory demands, and may consider establishing a dedicated organization or task force to handle regulatory matters where necessary.
• Establish a post-incident management system to prevent the recurrence of incidents. As the proposed amendments strengthen sanctions for repeated incidents, companies should identify root causes and improvement measures and reflect them in their information security management systems to ensure that the same type of incident does not recur.







